dForce’s lending protocol, LendfMe, was drained for $25 million in a known smart contract exploit.
Key Takeaways
- Uniswap’s imBTC pool succumbed to a special exploit, draining the pool of $260,000 of liquidity. One day later, this exploit was recreated on LendfMe.
- The exploit was a known attack vector that takes advantage of a known smart contract vulnerability.
- dForce raised money from the likes of Multicoin Capital and Huobi five days ago, putting these investors under pressure.
- LendfMe deployed Compound’s copyrighted code, without consent, which may have contributed to a security lapse.
The DeFi news category was brought to you by Ampleforth, our preferred DeFi partner
Share this article
dForce’s money market arm, LendfMe, was drained of $25 million in a known smart contract exploit. The incident comes less than a week after a $1.5 million raise.
Market Eviscerates LendfMe
DeFi is an emerging niche within crypto, making it difficult for projects to implement vulnerability free code. But these difficulties are dramatically more pronounced when a project doesn’t fully understand the code it has deployed.
Uniswap’s imBTC pool was completely drained yesterday, raising the suspicions of on-chain investigators. The attack was done using a known exploit of ERC-777 tokens.
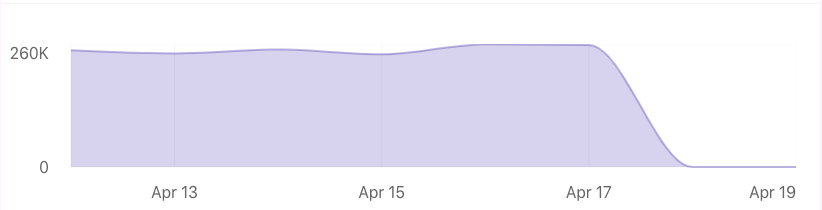

Today, LendfMe was emptied after a trader on the protocol managed to deploy a similar attack and drain the pool.
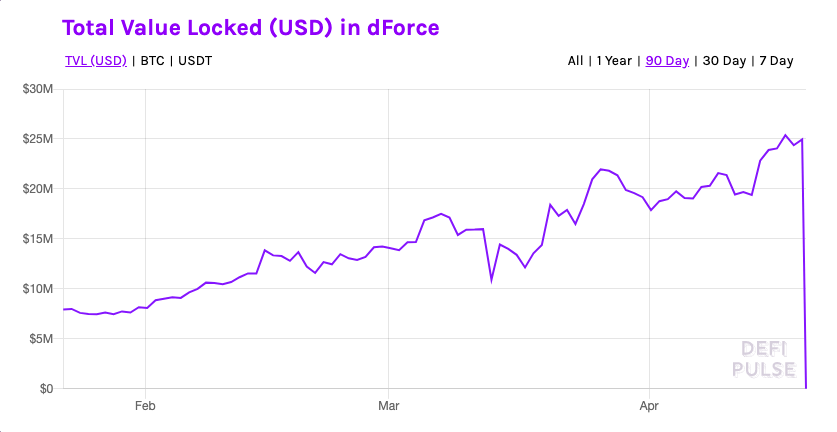

The vulnerability exploited on LendfMe was highlighted by ConsenSys for DEXes such as Uniswap. With ERC-777 token pools, a malicious entity can make constant contract calls to withdraw funds from the liquidity pool’s smart contract.
As a result, withdrawals are done faster than the balance can be updated, allowing an entity to purchase tokens for a steep discount by causing an imbalance to the liquidity pool. This very exploit was used to drain funds from the infamous Ethereum DAO smart contract in 2016.
According to dForce founder Mindao Yang, the hackers have attempted to contact the company and they “intend to enter into discussions with them.”
Recent dForce Investors Take a Hit
Four months ago, Compound accused LendfMe of plagiarizing its copyrighted code. Moreover, these accusations are substantiated. Reportedly, LendfMe didn’t bother to remove evidence of Compound’s license from its codebase on GitHub.
Despite the controversy, the project raised $1.5 million in capital in a financing round led by Multicoin Capital, announced just this week.
The rationale for investment was that dForce could cement its place as a leading player in the Eastern DeFi ecosystem. DeFi, however, is meant to be borderless, and is not restricted by geographic boundaries.
Users in China are not barred from using Compound, which was already three times more liquid than LendfMe before this incident.
dForce does have an edge through access to better channels for direct marketing and user on-boarding in Asia. But once again, it is critical to remind people that users in Asia can already leverage existing DeFi infrastructure.
If a project doesn’t have the expertise to develop it’s own smart contracts, and instead steals and redeploys somebody else’s copyrighted code, it’s a sign that they don’t have the capacity or intention to consider security.
Hope developers & users learn from the @LendfMe hack.
— 🤖 Leshner (@rleshner) April 19, 2020
Compound doesn’t support ERC-777 tokens yet, and perhaps for good reason. LendfMe’s deployment of stolen code may have contributed to the project’s lack of comprehension regarding complex security issues, leading them to succumb to the recent exploit.
“This attack was my failure. While I did not execute it, I should have anticipated it and taken actions to prevent it. My heart goes out to everyone harmed, and I will do everything in my power to make this right. I sincerely apologize to our users, to our new investors, and to my team for letting them down,” said Yang.