Key Takeaways
- The DeFi surge in 2020 led to more than a dozen hacks over several months.
- More than $50 million was lost due to bugs, exploits, and hacks.
- Although some losses were recovered, DeFi users need to stay vigilant when interacting with applications.
Share this article
DeFi is nothing short of a revolution. Automated blockchain-based financial primitives open a world of possibilities to disrupt traditional finance and make it more accessible.
This immense potential attracted a massive wave of users and investors to the space. In a matter of months, the total value locked (TVL) in DeFi protocols reached more than over $13 billion.
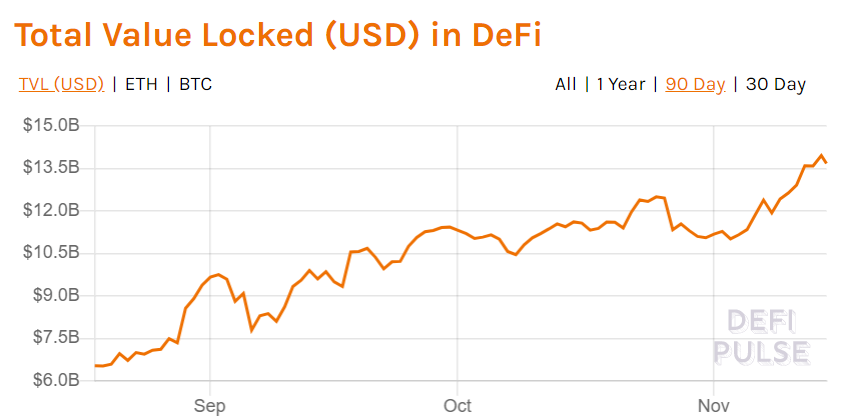
Meanwhile, activity on the DeFi epicenter blockchain, Ethereum, skyrocketed. The benefits appear to be endless, too.
Bringing financial activity on-chain allows for automation, trustless setups, and transparency.
However, it also creates numerous attack vectors, impossible in traditional finance.
DeFi Hacks
The majority of DeFi projects are open-source, meaning that code is easily accessible via GitHub for inspection both by well-intentioned and malicious users. If wrongdoers find bugs first, they can steal other users’ funds.
Besides bugs in code, DeFi applications are vulnerable to external exploits as well. DeFi’s efficiency mostly depends on composability, meaning that the more projects that are interconnected, the more value they can provide. Hence, exploiters can game the system and cause protocols to behave in ways not intended by developers.
The irreversibility of blockchain transactions exacerbates the situation. If hacks occur, funds are likely lost for good, though some projects will reimburse users from their pockets.
The following is a collection of over a dozen hacks and exploits within DeFi in 2020.
The Top 19 DeFi Hacks of 2020
1. bZx – $954,000
Although DeFi experienced explosive growth after introducing the Compound liquidity mining program, the space has been brewing since 2014. Many platforms existed and suffered from hacks before the DeFi summer of 2020.
bZx, a DeFi project focused on margin trading and lending, had a troubled start of 2020 with two consecutive hacks resulting in almost a million-dollar loss. The attacks occurred on Feb. 14 and Feb. 18.
Hackers didn’t find any bugs in bZx smart contracts. Instead, they exploited the interconnectedness of DeFi protocols. The exploit involved taking out flash-loans (borrowed and repaid in a single transaction) and manipulating asset prices to drain funds from lending pools by taking larger loans than was possible under normal circumstances.
The platform covered losses from its insurance fund, which receives 10% of all interest lenders earn.
2. dForce and Lendf.me – $25 million
On Apr. 19, a hacker took $25 million from a decentralized lending platform Lendf.me, which was functioning under the umbrella of the Chinese DeFi platform dForce. The hack used a well-known vulnerability of Ethereum, which was used in the infamous DAO Hack in 2016.
Ethereum’s ERC-777 token standard has a vulnerability, enabling an attacker to drain funds from some smart contracts holding them. An imBTC token that represented BTC on Ethereum was the ERC-777 standard, which allowed an attack vector.
Notably, the hacker returned stolen funds to Lendf.Me admin, which didn’t save dForce from criticism.
The same attack involving imToken occurred on Uniswap around the same time as on dForce, but hackers managed to drain much less – $300,000.
3. Hegic – $48,000
The options platform Hegic wasn’t attacked by anyone, yet a typo in the project’s code led to freezing users’ assets.
Traders and holders can use options on Hegic to insure against price volatility. Consider ETH is worth $500, and a user buys an option contract, which enables them to sell one ETH for 500 DAI within some time window. If ETH price tanks to $400, the user can safely exercise the contract, liquidating their position for 500 DAI.
On Apr. 25, Hegic published a warning about a typo in the smart contract, which led to freezing funds in unexercised contracts. If a user didn’t use their option, somebody had to unlock assets, but they couldn’t due to a typo.
Hegic’s founder reimbursed everyone who suffered.
4. Maker – $8 million
Maker found itself in a predicament after the crypto market crashed on Mar. 12. The platform ended up in over $8 million in debt as some of its loans were liquidated for free.
Since Maker is decentralized, it can’t use credit scores to verify the creditworthiness of its borrowers. Hence, loans on the platform are overcollateralized, meaning that a borrower supplies more assets that they can take out.
If the collateral value goes below a certain threshold, the loan is marked as undercollateralized, and liquidators can participate in an auction to liquidate the loan for a 13% reward.
When the market crashed, the activity on Ethereum soared as users panicked.
The network’s low throughput led to congestion, and many liquidators on Maker stopped working. Consequently, a handful of liquidators won auctions for free because there was no competition.
Blocknative, a forensic company, later published a report, saying that not only did users’ panic contributed to the congestion, but also malicious bot activity.
Bots spammed Ethereum with junk transactions that recursively replaced their existing transactions to slow other liquidators down and take advantage of the reduced competition.
5. Argent – $0
White-hat hackers found a severe vulnerability in the DeFi-focused mobile wallet Argent in OpenZeppelin on Jun. 18.
Argent replicates the experience of using a crypto wallet as a CC card with the concept of Guardians. Guardians are trusted devices with limited permissions to a user’s wallet, helping recover access to a wallet if the original owner loses access.
The uncovered vulnerability would have enabled hackers to freeze funds in wallets without Guardians. By the time the vulnerability was discovered, over 300 wallets with more than 160 ETH were at risk.
Fortunately, none of them suffered losses as the team implemented fixes in time.
6. Bancor – $0
Bancor, an app focused on asset swaps and conducted one of the largest ICOs of 2017, self-hacked to fix a critical vulnerability.
As a result of one of the system’s updates, users who interacted with the upgraded smart contract could lose their funds. $545,000 were at risk, but the Bancor team initiated a hack themselves to protect assets.
Besides the team, however, other white-hat hackers managed to drain over $130,000. Bancor got lucky, as it could have been malicious actors.
Bancor suffered from a large-scale hack back in 2018, and warnings about the new exploit had been floating around since Mar. 2020.
7. Balancer – $500,000
A decentralized exchange with customizable liquidity pools, Balancer saw an attack similar to what bZx suffered from. The incident occurred on Jun. 28.
The hack exploited a deflationary function of Statera (STA) token, which burns 1% of each transaction. The attacker used a flash loan to borrow a large amount of ETH and traded ETH against STA to decrease the number of STA tokens in the pool.
Once the amount of STA became very small, its price denominated in other assets in the pool surged so that the attacker could swap STA for other assets cheaply.
The team warned the community about the dangers of deflationary tokens before the hack occurred. However, as the protocol is permissionless, it couldn’t prevent users from adding unsafe assets.
8. Uniswap – $530,000
The initial decentralized exchange offering (IDO) of bZx protocol’s token BZRX on Uniswap highlighted the IDO model’s imperfections.
During an IDO, users send money directly to the team, and an asset’s price grows as a function of buying activity.
Less than a minute since the BZRX IDO started on Jul. 13, the price jumped 12x due to the front-running bot activity. Bots were placing buy orders in the same block that marked the start of the IDO.
Besides front-running buyers, the bots spammed the network so that users couldn’t push their transactions through.
How someone made a million dollar in 30 min?
1. Wait for BZRX news for uniswap listing.
2. Write a smart contract that buys token on Uniswap
3. Spam eth network to others can’t get in with failed txs— Roman Storm (@rstormsf) July 13, 2020
Once other buyers finally got in for the sale, the price was already high, and the bots’ owners took substantial profits. One early buyer made $500,000.
While the incident wasn’t a hack, it raised concerns about the viability and fairness of IDO models.
9. Opyn – $370,000
A smart contract bug allowed a double-spending attack, causing options protocol Opyn to lose $370,000 on Aug. 4.
The vulnerability was connected to the protocol’s native tokens called oTokens, which users burn when exercising options contracts. The contract couldn’t correctly exercise a batch of options, not burning oTokens at each closure.
Consequently, an attacker could reuse their oTokens balance and drain funds by exercising options for free.
According to PeckShield, a blockchain security company, a person with smart contract programming experience could easily spot the bug.
While the Opyn team couldn’t take down or change the smart contract, it managed to put the protocol on hold and save some of the users’ funds. On top of that, it announced reimbursements along with smart contract audits.
10. YAM – $750,000
A community-led DeFi stablecoin YAM managed to attract hundreds of millions of dollars in a matter of hours after it launched on Aug. 11, only to die days later due to a critical rebase bug.
YAM is a modified clone of Ampleforth, a stablecoin with dynamic supply. Depending on the demand, YAM and Ampleforth can increase or decrease the total supply to maintain the $1 peg. Supply is changed by calling a dedicated “rebase” function.
The team wanted to use YAM in the project’s governance, but the rebase function issued excess YAM tokens to the project’s treasury, which diluted YAM holders’ governance power.
Eventually, governance on YAM would be unusable.
The team tried to fix the bug by initiating a voting process to stop rebasing until the project’s governance contract is swapped. However, the initiative failed despite high voter turnout.
YAM’s key difference from Ampleforth is that it automatically bought yCRV tokens whenever supply increased. By the time the team realized nothing could be done to save the project, $750,000 of yCRV were already locked in the treasury.
The team didn’t give up and eventually swapped the project’s governance module to a working one. YAM holders could migrate via a temporary smart contract.
11. Soft Yearn – $250,000
Another rebase bug was exploited by a holder of Soft Yearn (SYFI) token on Sept. 3. The bug enabled a user to turn a $200 investment into $250,000.
Like YAM and Ampleforth, Soft Yearn dynamically changes its supply. However, the supply change didn’t translate to a Uniswap pool, where the token was traded.
A user with 2 SYFI in their wallet spotted the bug before others. After the rebase, they had more than 15,000 tokens worth more than 700 ETH at the time. The user took advantage of the opportunity that appeared in front of them and wiped all the SYFI pool liquidity by dumping all their tokens for ETH.
After the incident, the team published a rescue plan, which included relaunching SYFI tokens and adding 250 ETH to the Uniswap pool.
12. bZx (again) – $8 million
2020 didn’t go well for bZx, as it suffered three attacks. While the first two exploits involved manipulating external protocols, the third hack took advantage of an internal protocol flaw.
When users lend assets on bZx, they receive iTokens, which grow in value as a corresponding lending pool grows. The platform’s vulnerability enabled a hacker to mint iTokens without lending assets.
Consequently, the wrongdoer could exchange unbacked iTokens for the assets in bZx pools on Sept. 13.
The hacker managed to drain more than $8 million in various assets from bZx. However, the team tracked them down and retrieved stolen funds. Following the incident, the team joined forces with PeckShield to enhance bZx security.
14. Lien – $0
Lien Finance, a protocol focused on options and stablecoins, was on the verge of being hacked and losing $10 million in ETH. However, a group of white hat hackers discovered the vulnerability first.
As the report on Lien stated, the platform had a faulty function, which enabled minting large amounts of valueless tokens, which could then be exchanged for ETH stored on its smart contract.
How do you rescue 10 million dollars from a vulnerable smart contract without letting attackers know it’s there? Last Tuesday, @epheph, @sparkpool_eth, @tzhen, @wadealexc, and I found out.https://t.co/WOjO651VIw
— samczsun (@samczsun) September 24, 2020
After the white hackers discovered the vulnerability, they couldn’t perform a hack to save the platform’s money because front-running bots would have noticed their transactions.
The hackers communicated with Sparkpool, Ethereum’s largest mining pool. The Sparkpool team then made it possible to execute necessary transactions without revealing them to the bots, which saved 25,000 ETH from being stolen.
15. Eminence – $15 million
Andre Cronje became a superstar of the DeFi scene after launching the yEarn yield optimizer. The corresponding token, YFI, surged from 0 to tens of thousands of dollars in a matter of weeks. Consequently, many profit-seeking users started to closely monitor Andre’s activity to jump into his new projects before others.
One such project was a gaming platform named Eminence. After Andre mentioned its unaudited beta smart contract in a tweet, users threw $15 million into it. Since the contract was in the beta stage, it had a vulnerability, and hackers drained users’ funds by minting EMN tokens and selling them for more valuable assets on Sept. 28.
— eminence.finance (@eminencefi) September 28, 2020
The hackers subsequently returned $8 million in DAI to a smart contract controlled by Andre. The returned funds were used to cover some of the users’ losses.
16. UniCats – $140,000
A UniCats app with a yield farming feature had a backdoor, which enabled its developer to control users’ funds even when they withdrew money from the platform.
It’s common for DeFi users to connect their wallets to various DeFi apps, granting them access on different levels. UniCats asked users to permit spending an unlimited number of tokens. An anonymous user Jhon Doe granted UniCats the requested permission and lost $140,000 on Oct. 4.
According to a ZenGo crypto wallet report, Jhon wasn’t the only one who suffered from the exploit. Other users brought the malicious developer of UniCats at least $50,000 more.
If you are not yet convinced that you should NOT be approving infinite tokens to some random smart contract/Dapp, here’s a story of how Jhon Doe lost $140K worth of UNI in their sleep.
1/
👇 pic.twitter.com/QltkevnzDY— Alex Manuskin (@amanusk_) October 5, 2020
The hacker took care of their security and used several measures, including swapping addresses and using the crypto mixer Tornado Cash to cover their tracks.
17. Harvest – $24 million
A yield aggregator Harvest received critiques about its centralization before it got exploited for $24 million. Some of the users were concerned about the safety of $1 billion of assets locked on the platform, but the developers failed to change anything.
Shortly after the debates on the protocol’s centralization, $24 million were drained from Harvest due to an exploit on Oct. 26. In theory, a hacker could steal more.
The attacker used flash loans to manipulate stablecoin prices on the decentralized exchange Curve and used arbitrage to buy more stablecoins than they would normally be able to.
Like in the case of Eminence, $2.5 of the stolen funds were sent back to developers. The hacker swapped the rest for renBTC and sent BTC to other addresses. The RenBTC team helped Harvest identify the target addresses, which were then communicated to major exchanges for monitoring.
The team offered a $100,000 bounty to find the wrongdoer, but no one was turned in.
18. PercentFinance – $1 million
PercentFinance, a lending platform forked from the industry-leading Compound, froze $1 million of assets on Nov. 4. According to the team’s post, half of the funds belong to the project’s mods.
Users funds on our platform amounting to ~$1m are stuck in money market smart contracts
Reaching out to @WrappedBTC and @circlepay/@coinbase respective teams to help us make affected USDC/WBTC holders whole
Read Below:https://t.co/63Q1DlyqVv
— Percent Finance (@PercentFinance) November 4, 2020
The project’s vulnerability was inherited from Compound’s old smart contract, which developers forked. One of the developers decided to upgrade the smart contracts, but after doing so, they realized that transactions to the new contracts couldn’t be signed.
Hence, the old contracts were broken.
The team now hopes that issuers of the locked funds, which include centralized USDC and WBTC, can blacklist the addresses with blocked assets and issue new tokens for users who suffered from the bug.
The team also offered to launch new lending contracts, enabling 73% of USDC lenders’ funds after borrowing their loans. The lost WBTC are frozen forever if WBTC-issuer, BitGo, doesn’t help the PercentFinance team. ETH is lost without a chance for recovery.
18. SharkTron – $260 million
SharkTron, a DeFi platform featuring liquidity mining on Tron, had an incident according to a statement Tron Foundation issued on Nov. 9.
(1/2) Regarding the shark incident we have contacted @Binance and worked together on chasing down the funds and people behind this. A portion of the funds have been frozen on Binance.
— TRON Foundation (@Tronfoundation) November 9, 2020
Some sources report a loss of $260 million of users’ assets from several platforms associated with SharkTron, including Shark Invest and Shark Dice. Some users attach screenshots of wallets, which suffered losses.
Tron Foundation claimed that it joined forces with Binance and frozen some stolen funds on the exchange. On top of that, it promised to track down and freeze the remainder of the funds.
It advised users to file reports to the police in the meantime.
19. Akropolis – $2 million
Until it was hacked on Nov. 12, Akropolis provided its users with convenient deposit-and-forget pools, which automatically invested users’ funds and generated yields. When a user deposited their funds in a pool, they got ownership tokens in return.
A hacker noticed that Akropolis smart contracts didn’t have a whitelist for ERC-20 tokens, which can be deposited to the savings pools. To take advantage of this vulnerability, a hacker created a fake ERC-20 token and took out a flash loan of 800,000 DAI on the dYdX lending and trading platform.
By depositing fake tokens and the real DAI, the hacker managed to get twice as many ownership tokens as they normally would. Hence, they withdrew funds they didn’t have access to.
Akropolis didn’t admit the hack immediately. Moreover, the platform’s smart contracts were separately audited by two blockchain security firms.
At the time of writing, Akropolis’ stablecoin pools are frozen. The team is seeking ways to reimburse damages.
2020 Hacks: Closing Thoughts
Decentralized setups are liberating, yet they impose tremendous responsibility on users. While some teams strive to save users’ funds or recover losses, there are no safety guarantees.
Anyone interacting with DeFi protocols and crypto, in general, should be vigilant and mindful of their activity. It’s a wild west, no code is flawless, and everyone’s wallet is potentially a honeypot, so precautions should be taken.
During its short but bright history, DeFi has seen multiple hacks, vulnerabilities, and exploits of small and large platforms, which sometimes led to irreversible damage.
As the space progresses, it will see more incidents despite advances in tech and security. Hence, DeFi users should develop appropriate behavioral patterns to stay safe.
Share this article
290 Hacks Have Robbed the Crypto Industry of $13 Billion, Says Researc…
Crypto hackers have looted the industry of more than $13 billion in 290 different hacks, according to blockchain security firm Slowmist. As the market enters bullish territory and the size…
bZx Recovers $8.1M Lost in Third Exploit
Less than two weeks after re-deploying on mainnet, bZx was exploited for $8.1 million of LINK, ETH, and stablecoins. The incident caused the BZRX token to fall over 30%, as…
Hackers Drain DeFi Protocol Harvest Finance of $24 Million
A $24 million DeFi hack involving Harvest Finance has exposed the vulnerability of the entire DeFi ecosystem. Economic Exploit of Harvest Finance Working as a yield aggregator, Harvest Finance provides…

